 |
| from here and here |
Y'know, with a name like "ran somewhere" you'd think the process would be faster.
 |
| found on Izismile |
I'm not going to pretend that you can't remain safe while downloading things you shouldn't be downloading, however, it's I think it's fair to suggest that children probably can't do it.
 |
| from here and here |
125 million phones could cover more than a third of the population of the entire United States, and yet I've never even heard of the company Kochava before. If this single unknown company is tracking that many people, just think of how many people are being tracked by all the other unknown data brokers out there.
 |
| Product Page |
If you've ever seen anything like this then you've encountered geo-blocking, which is one of the few remaining good reasons to use a VPN. Unfortunately there are no VPNs for real life, so this is going to be like a splinter in people's minds.
 |
| from here and here |
Of course heartless corporations are going to double-down on their toxic business practices, but don't listen to their arguments. Ads have been a security threat for a long time, and if an advertising company hasn't come to terms with that fact about the Internet yet then they don't deserve your attention.
 |
| found on Imgflip |
This is quite an apt comparison. "Investing" in cryptocurrency is very much a gamble, and there are many ways for you to lose everything. Maybe it would be safer if people treated it like gambling instead of investing, and only put into it as much money as they can afford to lose. Of course there are still people with gambling problems who lose everything that way too, but at least people would have a better idea of what they were getting into and what kinds of risks are involved.
 |
| from here and here |
It's not the first time and it won't be the last time that ransomware operators proved themselves to be untrustworthy. I know it's a tough position to be in, but if you get compromised you have to prepare for the possibility that the data will be leaked. Paying the people who attacked you to not make things worse has no guarantee of success. Why should they keep their word once they have what they want? It's not like they're honourable, they wouldn't have attacked you in the first place if they were.
 |
| found on Reddit |
I don't know about you, but I certainly use Google in incognito-mode. Not even specifically dumb questions, but all the time. One of these days I'm probably going to have to figure out how to make every browser window an incognito window.
 |
| from here and here |
It's hard to believe anyone could give Facebook a run for their money, but it sounds like Oracle is doing just that. Not in the context of social networking, however, but rather in the context of global surveillance.
It's difficult to imagine why Oracle would be interested in my political views and physical location, but I suppose those are details an authoritarian regime could use about it's citizens.
 |
| from here and here |
When it comes to copying what you find online, I always advise people to learn from the code rather than simply copying it. Copying may be expedient, but it's risky too. If you don't understand the code you're copying then you run the risk of using it in inappropriate ways, including using compromised encryption keys like the folks at Hyundai appear to have done.
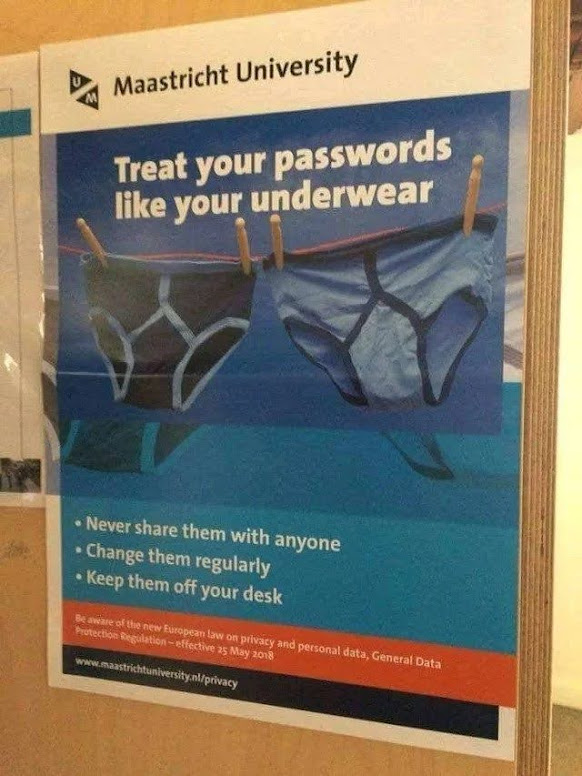 |
| found on Reddit |
Treating your passwords like your underwear is certainly fertile ground for humour, but it begs the question: do your passwords pass the sniff test?
 |
| from here and here |
There are so many allegations made in this whistleblower complaint that subverting transparency reporting is really just the tip of the iceberg, but it certainly seems novel to me.
 |
| Product Page |
 |
| Product Page |
Asking that people respect your privacy is getting harder and harder these days, but how can anyone argue with a cute kitten flipping you the bird?
 |
| from here and here |
The government is no more likely to hand over vulnerabilities for fixing than they are to lay down their arms, even though that makes us all less secure as a result. Don't count on their help to make software more secure when they have vested interest in it remaining vulnerable.
 |
| found on Acid Cow |
Security cat is going to be watching you swipe your card very carefully, so there better not be any funny business or things will get hairy.
 |
| from here and here |
If you have Zoom then you better get patching, again. The patch from earlier this week wasn't good enough but now they've got it for sure this time, honest.
 |
| found on Acid Cow |
You often can pull the faceplate off if a skimmer has been installed, but they're usually much smaller than this.
 |
| from here and here |
If you received the gift of poop and wondered who sent it, finding out may now be possible. Anonymity was necessary for a site like this because taking an action like this has consequences, and now those consequences can play out because the anonymity has been lost.
 |
| from here and here |
Candid Camera and all the hidden camera shoes that came after it were always a little creepy when you think about them secretly recording people without their prior consent. That's pretty much the same thing that the new surveillance comedy show from Amazon will be as well, except this time the cameras will be everywhere, and it will give people yet another reason to participate in a surveillance state that feeds data directly to police without permission.
 |
| found on Reddit |
You should definitely use an adblocker to protect you from malware served through ad networks, but maybe not that particular adblocker. It seems to have a conflict of interest.
 |
| from here and here |
I've heard that one of the reasons victims pay is that it can be faster to pay the ransom and decrypt the data than to restore from backups, but if it can take hours for a bitcoin transaction to go through then maybe that argument isn't so clear-cut after all.
 |
| Product Page |
A very simple design idea. I wonder if they also make a balaclava.
Anyway, it's a black hat, but if you find yourself identifying more with a white hat, they have those too.
 |
| from here (image source) |
I know it's not that we don't value privacy, but there are certainly times when we don't act like we value it. Public washrooms a good example of that. For all the problems they have it seems like no one is trying to design them better and some people are obviously designing them worse.
 |
| found on Izismile |
Look, I get it, passwords are hard to remember. However, if you have the sort of job where people visit you at your desk or worse where you give television interviews on TV, then this is not the memory aid you should be using. Put it in your wallet if you must, but not out in the open where anyone (everyone) can see.
 |
| from here and here |
Y'know, if I took nuclear secrets home with me, I'd definitely expect the authorities to show up looking for them. That Trump managed to act surprised is a testament to his skill as a con-artist.
 |
| found on The Funny Beaver |
I think every dog owner has experienced this. If they see you with food they are going to watch you like a hawk. Kiss your privacy goodbye until they see you finish it.
 |
| from here and here |
It's always a good idea to be suspicious of any strange behaviour on your computer. It might be innocuous (like Windows Update slowing everything down from behind the scenes) but it might also be a sign that your computer has been compromised. The only way to find out is to investigate further, but that won't happen if you don't at least have some suspicion about it.
 |
| from here and here |
So both Tim Hortons and the RCMP have been spying on people. I'm starting to wonder about my home and native land. Is everything spying on me? Are even those damn geese spying on me?
I suppose technically neither Tim Hortons nor the Royal Canadian Malware Purveyors are actually spying on me because I don't have a mobile phone for them to attack (and people question my decision to forgo cell phone ownership).
 |
| found on Izismile |
I think the youth of today know better than to get into a strange van for some free candy. Funny pictures, on the other hand, might not trigger the same suspicion since it wasn't explicitly drilled into anyone's head.
 |
| from here and here |
And if you use a 2nd VPN, what hides your browsing from that? A 3rd VPN? Eventually you're going to have to trust someone with your browsing traffic. Maybe instead of using a VPN you could just switch to an ISP you trust.
 |
| Product Page |
Consider this apparel the next time you have to travel to a user's desk to deal with a malware alert. You can start the conversation by just pointing at your torso.
 |
| from here (image source) |
The only reason you'd want to lock up your ice cream is if someone you live with, someone who shares physical access to your freezer, was eating it and you didn't want them to. This isn't going to stop them. It's only going to upset them and that's not good when you're living with them. I would think twice before employing this technique if I were you.
 |
| found on Funny Junk |
Privacy is, unfortunately, something that can be pretty easily violated simply by disregarding social norms. In this case, however, there are all kinds of possible solutions (a taller fence, a paintball, a high powered laser pointer, a well aimed/focused solar cooker, etc.)
 |
| from here and here |
True story. It wasn't even my job, but when you're one of the few people able to help it kinda becomes your responsibility. I did try to get my employer to donate to the maintainer of the service that identified which decryptor to use, but I never thought to ask for a raise or bonus for myself. Apparently some people think that was a missed opportunity.
 |
| found on Funny Junk |
Protection often isn't free. You have to consider those costs against the value of what you're trying to protect and the likelihood that it needs protection. Now I'm not trying to say Mr. Whiskers here isn't worth $24k, but that is a lot of money to spend protecting a rodent against a threat it's unlikely to face, or a threat that can be mitigated more easily and cheaply by keeping him in his cage out of harm's way.
 |
| from here and here |
One the plus side, I do get fewer useless alerts than I used to, but the useless ones still outnumber the useful ones by a wide margin. I don't even remember the last time I got a useful one. These days it's usually Windows telling me the firewall is disabled when it's perfectly fine.
Maybe I don't see useful alerts because the attacks never reach the computer with the firewall software in the first place. Maybe NAT-enabled routers were all most of us ever really needed.
 |
| from here and here |
People are really bad at creating strong passwords, so you might as well let the computer do it for you, and let it remember them for you while it's at it.
 |
| found on Imgur |
While that might stop me, I suspect that not only are there plenty of millennials who can drive stick there are also plenty of older people who steal vehicles.
 |
| from here (source article) |
I haven't made a secret about my feelings towards the Internet of Shit, but most of the time those connected objects at least provide the user with some compelling reason to use them. Often they give the user some novel feature or make something more convenient.
This scarf doesn't do any of that. It provides no extra functionality to the wearer beyond what a normal scarf would. You don't get to see the data, only some 3rd parties do. The best case scenario is that maybe someone will pay you to wear it, and you better hope they do because by extracting biometric data out of it they are definitely getting something of value in return.
.jpg) |
| Product Page |
Y'know, there was a time when I was prone to talking about my nerdier interests. I should probably try to be like that again... as soon as it's safe to be around people.
 |
| from here and here |
I mean, when you factor in the fact that Google is an ad company, their desperation to keep tracking people makes sense, but it's still desperation, and each year they drag out the end of tracking further just looks more and more desperate.
 |
| found on Reddit |
One bump in the road / one password breach and it's all over.
That's not to say that you couldn't have come up with a secure password when you were 7 years old, but rather if everything is dependent on that one password then it's a single point of failure. A single password breach would expose all of your accounts.